Roles and Authorization – The Often-Neglected Aspect of a S/4HANA Migration Journey
16 May 2025


Ramesh Menon
Director - Technology PracticeRamesh Menon is the Director – DIS Practice at Applexus, with over 24 years of experience in IT and non-IT industries. A certified RISE with SAP...
Migrating to SAP S/4HANA is a strategic transformation that modernizes system architecture, streamlines operations, optimizes workflows, and drives smarter, data-driven decisions across the enterprise. While organizations often focus on performance improvements, cloud benefits, and cost savings, one crucial aspect is frequently overlooked: Roles and Authorizations.
With thousands of transaction codes getting removed or consolidated, existing roles must be carefully evaluated to prevent compliance failures, security risks, and operational disruptions. Administrators need to account for new transactions and authorization objects to ensure users have the right access without excessive privileges.
For example, the Business Partner (BP) model in SAP merges vendor and customer master data, replacing multiple legacy transactions. Without proper role adjustments, users may either lose essential access or gain unintended privileges, increasing security vulnerabilities. Secure role migration isn’t an afterthought—it’s essential for protecting data, ensuring compliance, and maintaining business continuity.
The Hidden Risks: What Happens If You Ignore Proper Roles & Authorization?
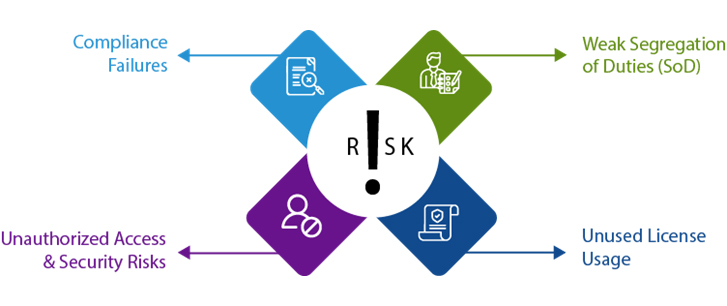
Organizations that neglect roles and authorization security in their S/4HANA migration face several risks:
Compliance Failures
Regulatory frameworks such as SOX, GDPR, and HIPAA require stringent access controls. Poorly managed roles can result in non-compliance, leading to severe fines and reputational damage. If organizations cannot provide an audit trail of access logs or prevent unauthorized access to sensitive data, they risk failing compliance checks and face significant financial penalties.
Weak Segregation of Duties (SoD)
Inadequate SoD policies may allow employees to perform conflicting actions, enabling fraud. For example, if an employee can both create and approve invoices, they could process fraudulent transactions unnoticed. Enforcing SoD controls and implementing real-time monitoring are crucial to mitigating financial and compliance risks.
Unauthorized Access & Security Risks
Misconfigured roles can grant unauthorized users access to critical data, increasing the risk of data breaches, intellectual property leaks, and insider threats. If an HR employee retains access to payroll systems post-departure, they could manipulate or extract sensitive data. Organizations must regularly review and remove unnecessary access privileges.
Unused License Usage – Impact on Total Cost of Ownership (TCO)
Over time, organizations often accumulate users with overly broad SAP access, resulting in inflated licensing costs under the RISE framework. For example, users who primarily engage in approval workflows or self-service tasks typically align with the Self-Service User category (1 Full User Equivalent (FUE) for 30 users). However, legacy role assignments—stemming from outdated job functions or historical needs—may inadvertently classify these users into more costly licensing tiers.
This misalignment can shift users into the Advanced User category (1 FUE per user) or even the Development User category (1 FUE per 0.5 users), significantly increasing total cost of ownership. To control licensing expenditures effectively, it is imperative to routinely assess user roles and adjust access based on current job responsibilities.
A well-structured role and authorization strategy mitigates these risks while delivering business benefits:
Enhanced security through least-privilege access enforcement.
Improved regulatory compliance with structured audit trails and SoD policies.
Reduced operational disruptions by ensuring seamless role transitions.
Increased efficiency by eliminating redundant access approvals and security-related support tickets.
Lower TCO
The Right Approach to Secure Role Migration
A well-structured and strategic approach is essential for a smooth, secure, and compliant role migration during your transition to SAP S/4HANA. Proper planning minimizes security risks, prevents operational disruptions, and ensures compliance with regulatory requirements.
Key Steps in Secure Role Migration
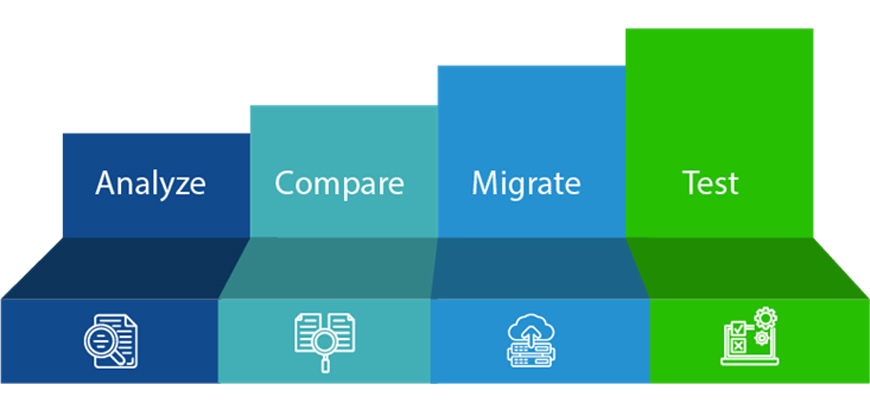
Analyze – A thorough assessment of existing roles, authorization objects, and security gaps is the first step. This involves identifying outdated or redundant roles, evaluating the impact of transaction code consolidation, and reviewing user access patterns to pinpoint security risks. Additionally, mapping existing roles to S/4HANA’s updated security model ensures a seamless transition.
Compare – To align roles and authorizations with S/4HANA, it is important to identify structural differences in authorization concepts. This includes mapping legacy transactions to new Fiori applications and comparing security requirements with the updated functionalities in S/4HANA. Ensuring these alignments prevents inconsistencies in access control.
Migrate – Role migration should be standardized and error-free, leveraging automation for efficiency. Retaining existing roles with minimal adjustments is suitable for organizations that already have a well-structured and effective security model in place. For companies aiming to ensure optimal security and compliance, redesigning roles from scratch offers a fresh start to build robust access controls aligned with current business needs. Alternatively, a balanced approach—enabled by tools like Applexus CeleRITE—allows for role optimization supported by automation. This method ensures a structured transformation of roles while minimizing disruptions to ongoing operations, combining the strengths of both preserving stability and enabling strategic improvements.
Test – Rigorous validation is necessary to maintain access control integrity and regulatory compliance. This includes running security checks on migrated roles, conducting user acceptance testing (UAT) to confirm correct access provisioning, and performing compliance validation to ensure adherence to standards like SOX, GDPR, and HIPAA.
How CeleRITE’s Access Control Migration Studio Helps
CeleRITE’s Access Control Migration Studio provides a comprehensive solution for securing and automating the migration of user roles across SAP systems. With its powerful set of features, the studio ensures a smooth and efficient transition to S/4HANA, identifying and mitigating risks while enhancing compliance. By automating key processes, enforcing real-time compliance, and offering data-driven insights, CeleRITE simplifies the role migration process, ensuring minimal errors and faster deployments.
Key Features
User & Role Analysis – CeleRITE provides detailed insights into an organization’s role and user landscape by identifying active and inactive roles, distinguishing between custom single and composite roles, and analyzing user activity. It helps organizations understand how many roles are actively used versus those that are dormant, breaking them down further into their structural type single or composite. Similarly, it assesses user activity by highlighting how many users are active or inactive in the system. These findings enable data-driven decisions for role cleanup, user de-provisioning, and overall access optimization, supporting a more secure and efficient system landscape.
Role Security Analysis & User & Role Carveout – Evaluates role structures to find security vulnerabilities and extracts specific user and role data subsets for focused analysis or migration.
User & Role Decommissioning – Efficiently removes obsolete users and roles to streamline access control and reduce unnecessary security exposures.
User & Role Remediation – Resolves misconfigured permissions, security issues, and compliance gaps to ensure proper role and user configuration.
User & Role Comparison – Compares users and roles across systems to highlight permission differences, maintaining consistency and security.
Role Standardization – Establishes consistent naming conventions, role structures, and permissions to simplify and secure access control management.
User & Role Transformation – Adapts roles and permissions for evolving business needs while ensuring continued security and compliance.
User & Role Migration – Facilitates seamless role and user migration across SAP systems, ensuring data integrity and continuity of business operations.
User & Role Optimization – Optimizes roles for efficiency, security, FUE usage and compliance, reducing complexity and enhancing overall SAP system performance and TCO.
CeleRITE also provides a range of additional functionalities to further support organizations during their migration journey. These include Automated Role Optimization to map roles to new S/4HANA structures and eliminate redundant permissions, and Compliance & Risk Reports like Role Usage & Optimization Reports, SoD Conflict Reports, and Access Violation Logs to ensure continuous monitoring and compliance. Additionally, the Role Transformation Summary offers visibility into role adjustments during the migration, while Seamless Migration & Continuous Monitoring guarantees a structured migration approach with proactive risk mitigation and ongoing security oversight.
Case Study
In one of the success stories of using CeleRITE’s Access Control Migration Studio, the client went through a comprehensive analysis of their access control system. They discovered that a significant portion of their roles were inactive or redundant, with 71% of custom composite roles and 2% of custom single roles showing as inactive. Additionally, we identified that 71% of users had been inactive, posing security risks.
By removing unused users and ensuring only active ones were migrated, we helped eliminate vulnerabilities and reduce security risks. Through these efforts, our client achieved up to 60% automation in role remediation, enabling a secure, compliant, and streamlined transition to S/4HANA, ultimately improving both security and system efficiency.
Conclusion: Secure Your S/4HANA Migration Today
Ignoring roles and authorization security in your S/4HANA migration can result in severe compliance failures, operational disruptions, and security breaches. A proactive and structured role migration strategy—backed by automation tools like CeleRITE’s Access Control Migration Studio—ensures a secure, compliant, and seamless transition.
Get in touch with us today for a demo and safeguard your S/4HANA migration!











